Due to a misconfiguration in their AndroidManifest.xml with their Task Control capabilities, Task Hijacking is a vulnerability that affects applications operating on Android devices.
This allows malware to take control of genuine programmes, steal data from users, and carry out a variety of attacks.
The Promon Security researchers have called this StrandHogg, while the original research report was presented at USENIX in 2015.
Understanding a few key terms
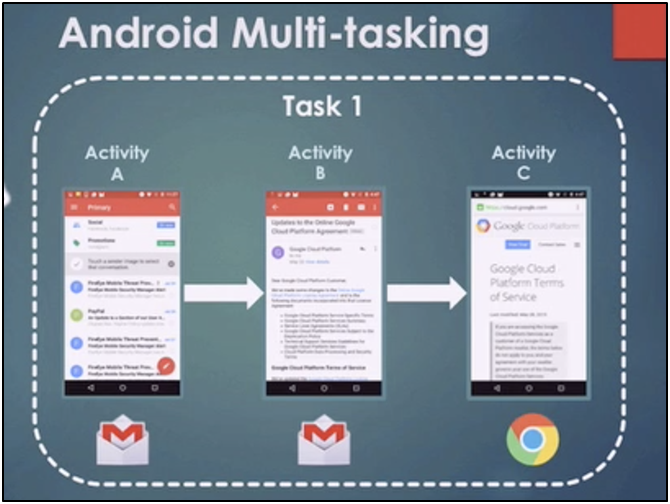
Task: — When doing a job, users engage with a task, which is a set of activities. The activities are organised in a stack (the back stack) in the order that they are opened.
Foreground Activities: — A foreground activity is the activity that is visible on the screen, and its task is known as foreground task. Only one foreground job is shown on the screen at a time.

(Simple Activity Flow)
1. Only Activity 1 is visible in the foreground.
2. Activity 2 begins, pushing Activity 1 to the back of the stack. Activity 2 is now in the Foreground/Front.
3. Activity 3 begins, pushing both Activity 1 and 2 to the back of the stack.
4. When Activity 3 is completed, the preceding action, 2, is automatically brought to the foreground. This is how Android task navigation works.
Android Multitasking- only one task
Launch Modes and Task Affinity
Task Affinity: — The AndroidManifest.xml file defines task affinity as a property in each activity> element. It indicates the Task an Activity chooses to participate in.
Every activity has the same affinity as the package name by default.
Launch Modes: — You may define how a new instance of an activity is related with the current task using launch modes. The activity’s launchmode parameter specifies how the activity should be launched into a task.
There are four launch modes to choose from:
· single top
· standard (default)
· single task
· single instance
When the launchMode is set to singleTask, the Android system considers three options, one of which is the cause for our assault. They’re here –
If an instance of the Activity already exists: -
Instead of establishing a new instance, Android resumes the current one. It signifies that in this mode, the system can only have one activity instance.
If you need to create a new activity instance: -
The Activity Manager Service (AMS) finds a “matched” task from all existing tasks to host the newly formed instance. If they share the same task affinity, an activity “matches” a task. This is why, in our malware/app, attacker’s we may provide the same task affinity as the susceptible app, causing it to run in their job rather than generating its own.
Without finding a “matching” task: -
The AMS generates a new task and makes the newly formed task’s root activity the new activity instance.
EXPLOITATION
The malicious software must be installed on the victim’s smartphone. He must then open it before proceeding to the vulnerable application. The malicious application will then be launched instead of the vulnerable application. If the malicious application uses the same login as the susceptible application, the user will have no way of knowing that his credentials are being used by a malicious application.
REMEDIATION
A easy remedy for this problem is to set taskAffinity=””. If the programme does not want other activities to join tasks that belong to it, the launch mode can be set to singleInstance. To override the default behaviour, a custom onBackPressed() method can be added.
Detox, are concentrate on the web application penetration testing service of your digital business. We help you to identify the risks in your application that safeguard you from data leakage, hackers, defamation, representational loss, and above all business loss.
Our experts have a wealth of knowledge in the field of Mobile app security testing. We help you to mitigate the threats linked with your mobile apps by identifying the vulnerabilities of your IOS and Android Operating systems.
Cyber Security Services Company || Cyber Security Professional Services || Cyber Security Solutions Company || Cyber Security Consulting || Cyber Security Consulting firms || Cyber security Service Provider || Best Security Testing Companies | Web Application Penetration Testing Service | Web Penetration Testing Services | Network penetration testing services | Security Testing Companies | Security Testing Services | Web Penetration Testing Company |Penetration Testing Companies | Penetration testing services |
- How Israel-Iran Cyber War Has Changed The Face Of Modern Warfare
- Understanding Task Hijacking in Android
- Top 10 Attacks And Vulnerabilities Of OWASP Mobile in 2022
- A Comprehensive Guide to OWASP Security Testing in 2022
- What is Web Application Penetration Testing Methodology
- 10 Types Of Cyber Attacks And How They Can Affect You in 2022
- What is Android app Pentesting in 2022- Detox Technologies
- How To Perform Security Testing Of Mobile Apps In 2022
- Top Reasons for using AI in Cyber Security
- How To Protect Yourself From Online Scammers In 2022
- 10 Warning Signs Of An Imminent Cyber Attack In 2022
- What Is Log4Shell? The Log4j Vulnerability Explained in 2022
- What Is Android App Pentesting Testing Methodology In 2022




0 Comments